Our Objective is to build a cyber security that benefits you without the hassles. Increasing Cyber Security Awareness and Countering Advanced Threats. IARM Will Never Let You Down
Friday, June 7, 2024
The Role of Managed Security Services in Enhancing Healthcare Cloud Security
Sunday, February 11, 2024
Enhancing Healthcare SIEM Incident Response: 7 Key Integrations
Friday, February 24, 2023
Is Your Connected Vehicle Safe from Cyber Attacks? Explore the Role of Cloud Security
Connected vehicles and smart transportation systems have been rapidly increasing in popularity due to their benefits in improving the efficiency, safety, and convenience of transportation. These systems rely on sensors, artificial intelligence, and cloud computing to process and analyse data that is collected from various devices, including traffic signals and other smart devices.
However, with the increased use of these systems comes an increased risk of cyber attacks, which could lead to disastrous consequences. In this blog post, we will explore the role of cloud security services in securing connected vehicles and smart transportation systems.
The Risks of Cyber Attacks on Connected Vehicles
Cybersecurity threats to connected vehicles include potential scenarios where vehicles can be hacked by malicious actors. For instance, hackers could take control of a vehicle's brakes, steering, or acceleration.
This could lead to accidents, injuries, and fatalities. Additionally, cybercriminals could steal sensitive data and personal information, such as geolocation data, driving habits, and credit card details. This could result in identity theft, financial fraud, and other malicious activities.
Cloud Security in Connected Vehicles
To ensure the security of connected vehicles, cloud security services and solutions play a vital role. Cloud computing provides a scalable and flexible infrastructure that can manage large amounts of data and improve the performance of connected vehicles. However, to ensure the protection of sensitive data, cloud security measures must be implemented.
Encryption, access controls, and firewalls are just a few examples of the security measures that can be used to safeguard against cyber attacks. Additionally, cloud providers should conduct regular security audits and maintain up-to-date security standards to ensure that their cloud services remain secure.
Ensuring Security in Smart Transportation Systems
Securing connected vehicles is not enough to ensure the safety of smart transportation systems. The infrastructure that supports these systems, such as traffic signals, road sensors, and other smart devices, must also be secured.
One way to achieve this is by using cloud security to protect these systems. By implementing security measures such as access controls, encryption, and firewalls, smart transportation systems can be better protected against cyber attacks.
The Future of Cloud Security in Connected Vehicles
As connected vehicles and smart transportation systems continue to grow, the future of cloud security will need to adapt to these changes. One such change is the emergence of autonomous vehicles, which rely heavily on cloud computing.
Cloud security measures will need to be developed and implemented to ensure the safety of these vehicles. Additionally, as smart cities continue to be developed, the infrastructure that supports these systems will need to be secured with cloud security measures.
Connected vehicles and smart transportation systems have become a reality in recent years, providing benefits in efficiency, safety, and convenience. However, these systems come with an increased risk of cyber attacks that could result in disastrous consequences.
Cloud security services play a vital role in securing these systems by protecting sensitive data and personal information, implementing security measures, and securing the infrastructure that supports these systems. As connected vehicles and smart transportation systems continue to evolve, the future of cloud security will need to adapt to ensure their safety.
Thanks and Regards,
Andrea - IARM Information Security
Vulnerability Assessment services || Cloud security services|| VAPT Service provider in India
Sunday, February 16, 2020
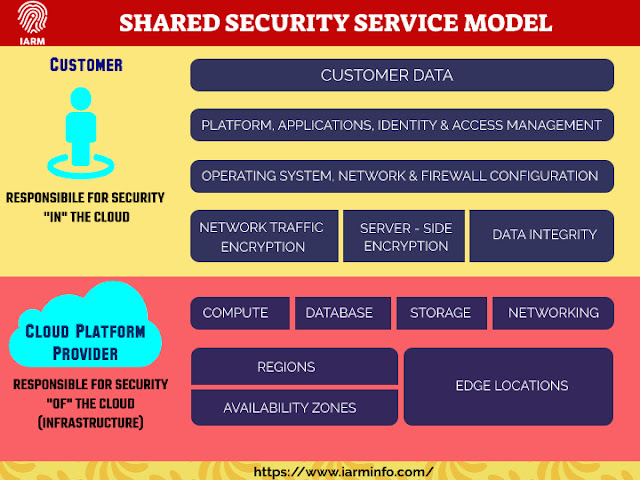
Shared Responsibility Model In Cloud Environment
CLOUD SERVICE PROVIDERS SHARED SECURITY SERVICE MODEL
Holding your information under tight lock and key requires the consolidated exertion of both our group and yours. Cloud Security Service Provider to guarantee everybody comprehends the common security model when working in the cloud.
Continue pursuing to figure out how, by cooperating, we can give better Cloud Data Security Solutions
Who can take responsibility for cloud security?
While Cloud Security Company In India guarantees our foundation's security and the assurance of your data, we as a whole bear some duty regarding total security all through your information's
Information Security Provider Company assists with defending the information that you store with us, however we have little authority over what occurs outside our condition.
In this manner, it's significant that you assess your own security approaches, consider how your clients get to your framework, screen how the information is utilized, and keep up the physical security of your own premises and its equipment.
To truly comprehend why security is a mutual obligation, you have to know the distinction between two key ideas:
Security of the Cloud – Security quantifies that we, your cloud Cloud Security Service Provider, will implement.
Security in the Cloud – Security estimates you, our customer, execute to defend your substance and applications
Cooperating is the best strategy for the security of your association's information.
By monitoring Information Security arrangements and making fitting moves, IARM, Leading Information Security Company is making a sheltered, secure condition for your touchy information.
In the event that you despite everything need more assistance understanding the common obligation model, converse with your association's IT group, keep in touch with us at binary@iarminfo.com or call 18001021532 (Toll Free)
Thanks and Regards
Priya
enterprise cloud security services | information security company in india | Cyber Security Company In Chennai |
Penetration Testing Company In Chennai | Information Security Auditing Company
Free SBOM Webinar: Learn How to Simplify Your Software Bill of Materials Workflow
Software security today depends on one essential ingredient— transparency . And nothing delivers that transparency better than a Software Bi...

-
In the fast-evolving landscape of healthcare technology, the Internet of Things (IoT) has emerged as a game-changer. From remote patient mon...
-
As 2024 draws to a close, it’s the perfect moment to take stock of the year’s journey and look ahead to the future. With technology advanci...
-
Disaster recovery is a critical concern for healthcare organizations due to the sensitive nature of the data they handle. Outsourcing SOC (S...
.jpg)
.jpg)

.jpg)

.jpg)