CLOUD SERVICE PROVIDERS SHARED SECURITY SERVICE MODEL
Holding your information under tight lock and key requires the consolidated exertion of both our group and yours. Cloud Security Service Provider to guarantee everybody comprehends the common security model when working in the cloud.
Continue pursuing to figure out how, by cooperating, we can give better Cloud Data Security Solutions
Who can take responsibility for cloud security?
While Cloud Security Company In India guarantees our foundation's security and the assurance of your data, we as a whole bear some duty regarding total security all through your information's
Information Security Provider Company assists with defending the information that you store with us, however we have little authority over what occurs outside our condition.
In this manner, it's significant that you assess your own security approaches, consider how your clients get to your framework, screen how the information is utilized, and keep up the physical security of your own premises and its equipment.
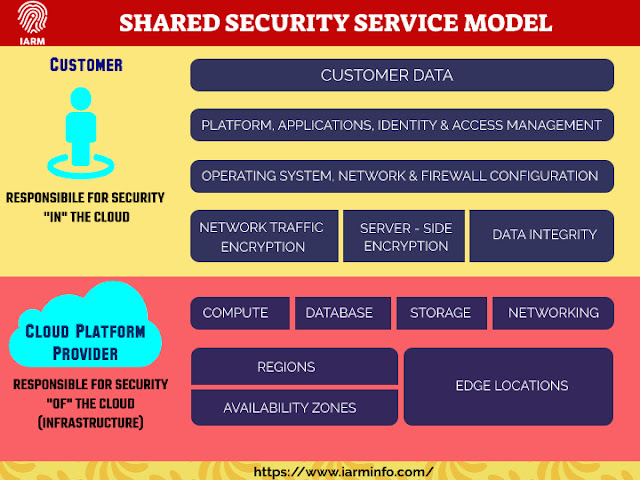
To truly comprehend why security is a mutual obligation, you have to know the distinction between two key ideas:
Security of the Cloud – Security quantifies that we, your cloud Cloud Security Service Provider, will implement.
Security in the Cloud – Security estimates you, our customer, execute to defend your substance and applications
Cooperating is the best strategy for the security of your association's information.
By monitoring Information Security arrangements and making fitting moves, IARM, Leading Information Security Company is making a sheltered, secure condition for your touchy information.
In the event that you despite everything need more assistance understanding the common obligation model, converse with your association's IT group, keep in touch with us at binary@iarminfo.com or call 18001021532 (Toll Free)
Thanks and Regards
Priya
Top It Security Companies | Cloud Security Service Provider | Network Security Solutions India | Soc Services In India |
enterprise cloud security services | information security company in india | Cyber Security Company In Chennai |
Penetration Testing Company In Chennai | Information Security Auditing Company
enterprise cloud security services | information security company in india | Cyber Security Company In Chennai |
Penetration Testing Company In Chennai | Information Security Auditing Company

.jpg)
.jpg)

No comments:
Post a Comment