Hello Folks!
Email security is a difficult one and having many sides, there is no extraction
to protect an organisation from the cybercrime attack such as phishing threat.
to protect an organisation from the cybercrime attack such as phishing threat.
What is Phishing?
Phishing is a technology and human problem that must be addressed by a combination of anti-phishing technology,
brand monitoring services, threat-intelligence services, staff phishing simulations and phishing awareness training.
brand monitoring services, threat-intelligence services, staff phishing simulations and phishing awareness training.
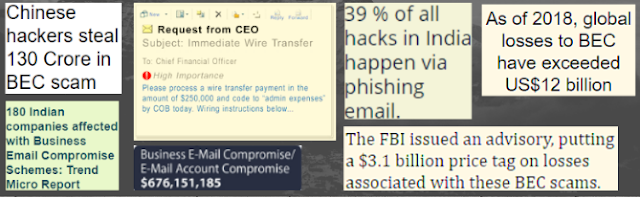
Business email compromise cases are CEO email frauds, executives inboxes are compromised with emails
containing malicious links, designed to mine company data.
Tips for how to identify BEC scam
- Top Subject lines in BEC scam Emails:
-Payment -Request -Urgent -Attention -Important -Tax In. -Wire/transfer -Greetings
- Top Attachment File Names in BEC scam Emails:
-Purchase order -Payment -Invoice -Slip -Receipt -Bill -Advice -Transfer
HOW DO YOU PROTECT YOURSELF OR YOUR COMPANY?
Cybercriminals monitor social media accounts (Linked.. Facebook. and Twitter) belonging to
executives/employees for any disclosure.
executives/employees for any disclosure.
Following that, IARM - Top cybersecurity Company in Chennai delivers the Vulnerability Assessment
and Penetration Testing services to protect the threads and cyber attacks. Advanced Penetration Testing
services for Artificial Intelligence and also delivers Pentesting for network, Cloud, Web and Mobile Application.
and Penetration Testing services to protect the threads and cyber attacks. Advanced Penetration Testing
services for Artificial Intelligence and also delivers Pentesting for network, Cloud, Web and Mobile Application.
Businesses can take a number of steps to prevent Business Email Compromise MEC):
-- Remove any sensitive online disclosures such as work emails and phone numbers. Avoid mentioning
the future whereabouts of company executives on social media accounts and company web pages. Executives
should hide their updates and posts from public view by increasing privacy settings.
the future whereabouts of company executives on social media accounts and company web pages. Executives
should hide their updates and posts from public view by increasing privacy settings.
-- Marketing / Finance departments should use unique Email ID rather than using generic email id like
finance@, sales@, etc. This will prevent such attacks as it will be difficult to guess.
finance@, sales@, etc. This will prevent such attacks as it will be difficult to guess.
-- Implement policies and procedures to handle emails requesting wire transfers or the release of sensitive
personally identifiable information.
personally identifiable information.
-- Use two-factor authentication in which approval of wire transfers will require two employees to authorize a
transaction. which increases the chances of detecting the scam.
transaction. which increases the chances of detecting the scam.
-- Educate organization people about BEE attacks. particularly executives or staff who have the authority to
release funds or critical information.
release funds or critical information.
If you want to know more about Information Security for your business, you can reach the Cybersecurity company in Chennai.
Technology Used
Sender Policy Framework (SPS)
It is an email validation system. designed to prevent unwanted emails using a spoofing system. It lookup the domain and
verifies that corresponding DomairOP is authorized to send an email for that Domain.
verifies that corresponding DomairOP is authorized to send an email for that Domain.
Does not prevent attackers from spoofing the "From" address.
Domain Keys idengRed (DKIM)
DKIM provides an encryption key and digital signature that verifies that an email message was not forged or altered but
this may not prevent attackers from spoofing the ‘From' address.
this may not prevent attackers from spoofing the ‘From' address.
Domain-based Message authentication, reporting, and conformance (DMARC)
DMA, Verifies the “From” domain matches the 'Return-Path' domain checked by SPF. Verifies the “From” domain matches
the "d= domain name' in the DKIM signature.
the "d= domain name' in the DKIM signature.
Get in touch with IARM to set up the technology part for any Organization. Visit: https://www.iarminfo.com/ and mail us at info@iarminfo.com for any queries
Thanks and Regards
Priya - IARM Information Security
CyberSecurity Company In Chennai | Information Security company In Chennai | Cyber Attack Recovery Services In India | VAPT Testing Company in Chennai | Penetration Testing Company In Chennai | Penetration Testing Services | VAPT Services in Chennai | Business Continuity Management services in Chennai | soc2 audit company in Chennai | Business Continuity Management services in Chennai | BCP services | Business Continuity Planning company | Cyber Recovery Solution In India | Cybersecurity services


.jpg)
.jpg)

No comments:
Post a Comment